TIL: How shodan takes screenshots of computers
Recently, I have been playing around with shodan images, a service provided by shodan that aggregates screenshots of accesible videofeeds over the internet of things, including a lot of windows login screens and webcams.
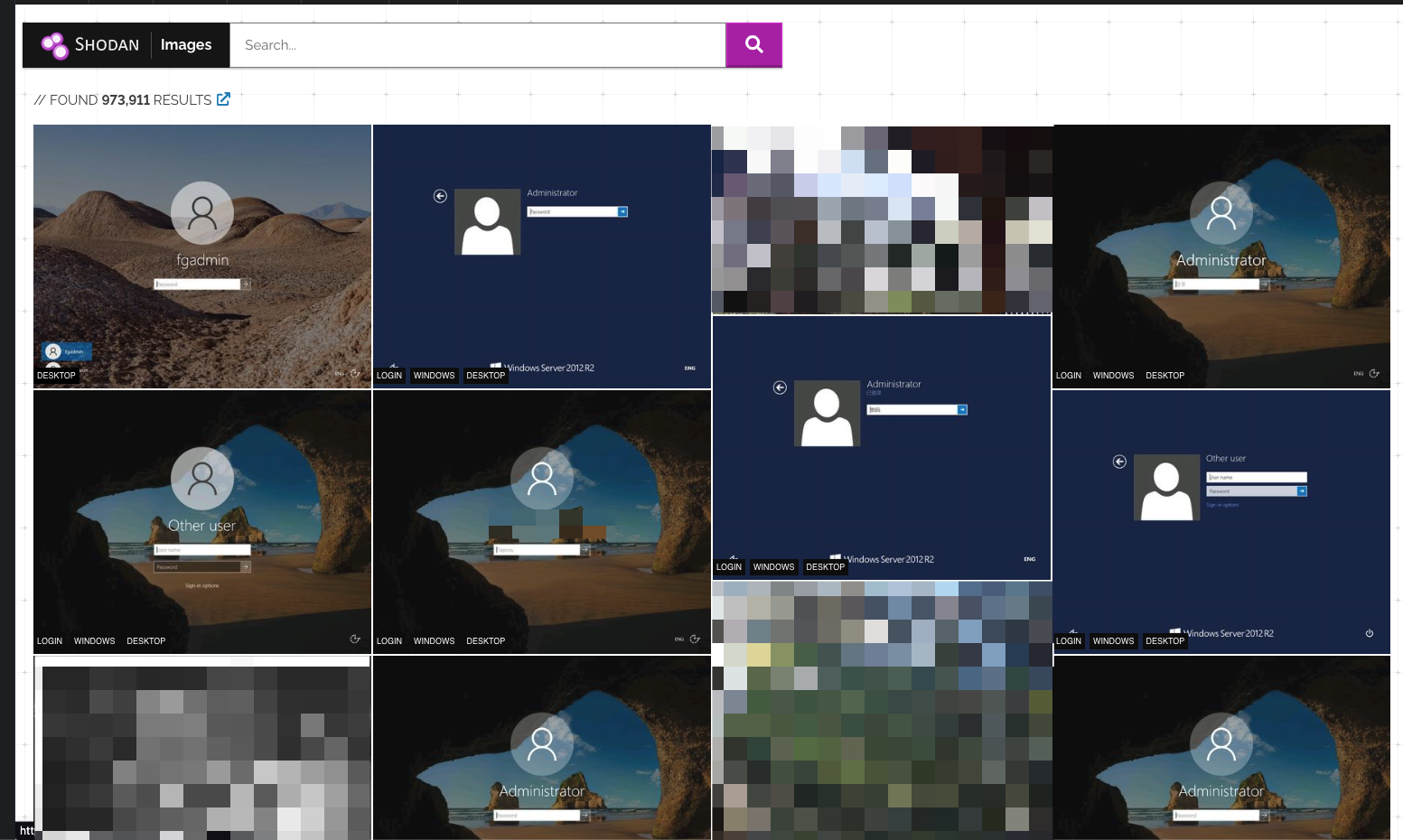
The catch is, while they provide the screenshot for the users, shodan provides absolutely no hints as of how they obtained the screenshot.
Shodan claims that they grabbed those screenshots based as the RDP service is exposed to the internet, but when I tried to access the remote desktops with Microsoft Remote Desktop, it immediately prompted me for a username and password, which I do not have.
After some digging on the internet, I came across this post on reddit, which says that the servers that have a login screen scraped by shodan doesn’t have Network Level Authentication enabled. While Microsoft RDP client enforces Network Level Authentication by default on the client side, it could be bypassed if the server doesn’t enforce it with a custom client.
While rdesktop was suggested, it seems to be unmaintained and brew wouldn’t let me install it. Instead, I came across freerdp, an actively maintained, fully featured, though less user friendly(CLI based) RDP client.
To access a RDP server without NLA, create a regular rdp file from the target machine’s ip address, and add the following line to the file:
enablecredsspsupport:i:0
Or, you can paste the snippet below, and switch <YOUR_IP_ADDRESS> for the target machine’s ip address
After installing freerdp (and xquartz if you’re on mac), simply run the follwing command:
xfreerdp ./sample.rdp
And voila, you should be able to access the login screen of the target machine just like shodan.
Yes, you still need the password in order to access the machine, but the ability to access the machine reveals all the user accounts so that hackers would only have to enumerate the passwords for that specific account, potentially revealing your identity information, and opens up more possibilities for further attacks.